Asking for the impossible
When it comes to electronic voting of any kind we are asking for the impossible of these systems. We are asking a county to produce the kind of security that even some of the top companies can't achieve with a far superior budget. Security in today's world is based on acceptable risk not 100 percent secure. When an election is decided by fewer than 1 percent what if just 1 percent of voters were impacted? It is unacceptable, so in the case of voting no risk is acceptable. This means traditional thinking on cybersecurity is out.
Pulse Secure VPN under attack 4-21-2021
Why does this matter? Today they are moving ballots and equipment in Maricopa County. We identified some of Maricopa Counties external facing systems use F5/BigIP for remote access.
Pulse Secure Critical Zero-Day Security Bug Under Active Exploit
"CVE-2021-22893 allows remote code-execution (RCE) and is being used in the wild by nation-state cyberattackers to compromise VPN appliances in defense, finance and government orgs."
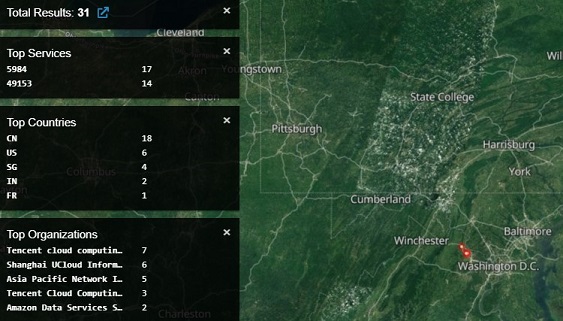
We noticed China has several honeypots setup with banners showing BigIP when we did a Shodan search for "Pulse Secure VPN."
"Server: BigIP Docker/1.13.1 (linux),docker"
- It's alarming that Tencent has a datacenter so close to Washington DC.
- They are actively targeting department of defense and other government targets.
- They have honeypots searchable on Shodan using the phrase "Pulse Secure VPN" all linked to the CCP. Every last one is Chinese.
- Some of these servers have headers for BigIP
- Maricopa County uses BigIP.
- They just started moving equipment on the day the Threatpost article comes out.
Here are some important details from this article that also matter:
The firm tracks those tools as the following:
- SlowPulse: Trojanized shared objects with malicious code to log credentials and bypass authentication flows within the legitimate Pulse Secure shared object libdsplibs.so, including multifactor authentication requirements.
- RadialPulse and PulseCheck: Web shells injected into legitimate, internet-accessible Pulse Secure VPN appliance administrative web pages.
-
ThinBlood: A utility used to clear relevant log files.
- Other capabilities: Toggling the filesystem between Read-Only and Read-Write modes to allow for file modification on a typically Read-Only filesystem; the ability to maintain persistence across VPN appliance general upgrades that are performed by the administrator; and the ability to unpatch modified files and delete utilities and scripts after use to evade detection.
UNC2630 targeted U.S. defense-sector companies as early as last August, Mandiant noted. It added that the activity could be state-sponsored, likely backed by China.
“We suspect UNC2630 operates on behalf of the Chinese government and may have ties to APT5,” according to the analysis. “UNC2630’s combination of infrastructure, tools, and on-network behavior appear to be unique, and we have not observed them during any other campaigns or at any other engagement. Despite these new tools and infrastructure, Mandiant analysts noted strong similarities to historic intrusions dating back to 2014 and 2015 and conducted by Chinese espionage actor APT5.”
This does not look good. If you are not concerned about the CCP at this point and believe Russia was the culprit you are ignoring facts.
If the election was hacked, we may never know beyond reasonable doubt that was the case.
"Even if someone figures out that the voting machine firmware has been changed, the votes may need to be tossed"
It's amazing how opinions change after elections. Mail-in ballots combined with powerful computer systems can be a very dangerous combination. That will always be the case.
"This Election Day voters in 10 states, or parts of them, will use touch-screen voting machines with rewritable flash memory and no paper backup of an individual's vote; some will have rewritable flash memory. If malware is inserted into these machines that's smart enough to rewrite itself, votes can be erased or assigned to another candidate with little possibility of figuring out the actual vote.
In precincts where vote tallies raise suspicions, computer scientists will be called in the day after the election to conduct forensics. But even if a hack is suspected, or proven, it would likely be impossible to do anything about it."
Are these systems secure?
Independent Security Evaluations
Back in 2014 Freeman, Craft, McGregor Group evaluated Dominion software for vulnerabilities. Not surprisingly, it didn't go so well for Dominion.
Def Con 27 evaluated various Dominion and ES&S systems in August 2019, see their report:
Encryption Claim Disputed by Court
Weak certificates and lack of certificate verification can create an opportunity for "man in the middle" attacks and can decrypt encrypted data using certificates. So if the above is true then we have voting systems with very little data protection.
Can you stop a state-sponsored attack?
Prevention is a tall order, assume you will get breached and ask yourself- what will come next? Are you able to detect a nefarious actor in your network? This is a scenario that every IT team running an electronic voting system should be prepared for. From what we have seen in these audits, they have not been are are not prepared to prevent or recover from a state-sponsored attack.