New Moriya rootkit used in the wild to backdoor Windows systems
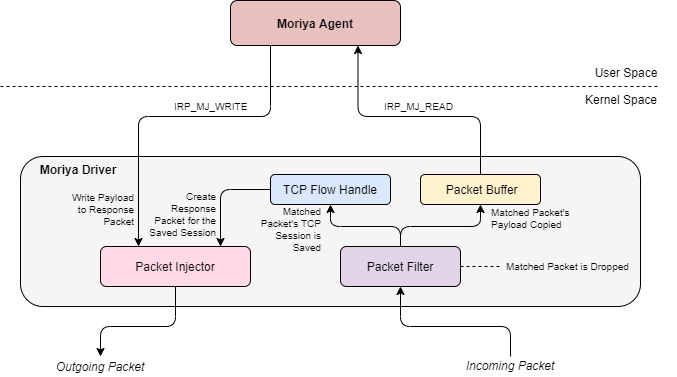
According to Kaspersky's telemetry, the malware was deployed on the networks of less than 10 entities in highly targeted attack
The threat actor used backdoored systems belonging to Asian and African diplomatic entities and other high-profile organizations to gain control of their networks and maintain persistence for months without being detected.
The attackers also deployed additional tools (including China Chopper, BOUNCER, Termite, and Earthworm) during the post-exploitation stage on the compromised systems (custom-made and previously used by Chinese-speaking actors).
This enabled them to move laterally on the network after scanning for and finding new vulnerable hosts on the victims' networks.
This is very relevant and a window into the CCP toolbox. Election systems most often are dependent on Windows. This is a tool that has been in use since 2018 and would have gone undetected by traditional endpoint protection.
Telegram Platform Abused in ‘ToxicEye’ Malware Campaigns

"Even if the app is not installed or in use, threat actors can use it to spread malware through email campaigns and take over victims’ machines, new research has found.
Hackers are leveraging the popular Telegram messaging app by embedding its code inside a remote access trojan (RAT) dubbed ToxicEye, new research has found. A victim’s computer infected with the ToxicEye malware is controlled via a hacker-operated Telegram messaging account.
The ToxicEye malware can take over file systems, install ransomware and leak data from victim’s PCs, according to researchers at Check Point Software Technologies.
Download “The Evolution of Ransomware” to gain valuable insights on emerging trends amidst rapidly growing attack volumes. Click above to hone your defense intelligence!
Check Point said it tracked more than 130 cyberattacks in the last three months that leveraged ToxicEye, which was being managed by threat actors over Telegram. Attackers use the messaging service to communicate with their own server and exfiltrate data to it, according to a report published online Thursday.
Hackers are likely have targeted Telegram, which has more than 500 million active users across the world, as their distribution platform because of its widespread use and popularity, said Idan Sharabi, research and development manager at Check Point.
“We believe attackers are leveraging the fact that Telegram is used and allowed in almost all organizations, utilizing this system to perform cyber attacks, which can bypass security restrictions,” he said in an e-mailed statement.
Researcher point out that Telegram—which is known as a secure and private messaging service–has become even more popular during the pandemic and especially in recent months. That’s because of new privacy and data management policies instituted by WhatsApp raising concern among users and pushing them by the millions to alternative messaging platforms like Telegram.
This growing Telegram userbase has led to a corresponding surge by attackers pelting the Telegram platform with a slew of common malware, researchers report. According to Check Point, dozens of “off-the-shelf” malware samples have also been spotted targeting Telegram users.
Researchers said Telegram is an ideal way to obscure such activity because it isn’t blocked by anti-virus protections and allows attackers to remain anonymous, requiring only a mobile phone number to sign up, researchers noted. The app also allows attackers to easily exfiltrate data from victims’ PCs or transfer new malicious files to infected machines because of its communications infrastructure, and to do so remotely from any location in the world, they said.
Infection Chain
The Telegram RAT attacks begin with threat actors creating a Telegram account and a dedicated Telegram bot, or remote account that allows them to interact with other users in various ways–including to chat, add people to groups or send requests directly from the input field by typing the bot’s Telegram username and a query.
Attackers then bundle the bot token with the RAT or other chosen malware and spread the malware via email-based spam campaigns as an email attachment. For example, researchers observed attackers spreading malware via a file called “paypal checker by saint.exe,” they said.
Once a victim opens the malicious attachment, it connects to Telegram and leaves the machine vulnerable to a remote attack via the Telegram bot, which uses the messaging service to connect the victim’s device back to that attackers command-and-control server, according to the report. Post-infection attackers gain full control over a victim’s machine and can engage in a range of nefarious activities, researchers said.
In attacks that Check Point observed, the ToxicEye RAT was used to locate and steal passwords, computer information, browser history and cookies from people’s devices; delete and transfer files or kill PC processes as well as take over a PC’s task manager; deploy a keylogger or record audio and video of the victim’s surroundings as well as steal clipboard contents; and use ransomware to encrypt and decrypt victims’ files.
Identification and Mitigation
Check Point said indication of infection on PCs is the presence of a file called “rat.exe” located within the directory C:\Users\ToxicEye\rat[.]exe.
Organizations also should monitor the traffic generated from PCs to Telegram accounts when the Telegram app is not installed on the systems in question, researchers said.
Researchers encourage hyper-vigilance when it comes to scrutinizing emails. Recipients need to always check the recipient line of an email that appears suspicious before engaging with it, Check Point said. If there is no recipient named or the recipient is unlisted or undisclosed, this likely indicates the email is a phishing or malicious message."
